Theharvester is a very simple, handy Linux based command-line tool that helps you locate domain-related email addresses in various databases or data sources such as google, google CSE, bing, bing API, PGP, LinkedIn,google-profiles, jigsaw, Twitter, and google plus.
It is one of those tools we use for information gathering during a penetration test engagement but because of its simplicity and useful information anyone can take advantage of it, be it that you’re researching a potential employer, looking for more information for a sale lead, or doing information gathering theharverster will help you find useful information in a short period of time.
Let’s go over and break down the following example:
theharvester –d microsoft.com –b pgp >ms.txt
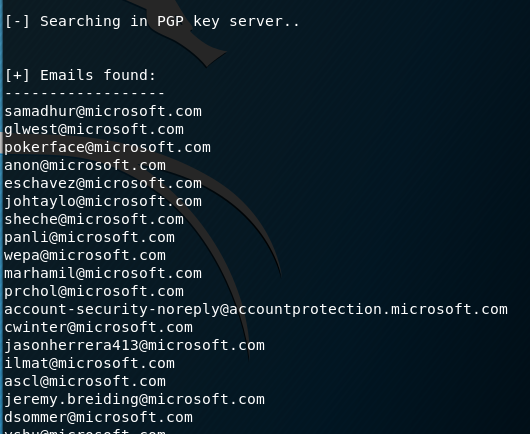
- theharvester: this is the command, just fyi it’s case sensitivity so make sure you type it in lower case.
- -d: tells the command the specific domain for the query.
- -b: tells the command what data source to use, you can list one data sources mentioned before or you can use “all” to query all data sources.
- >: redirects the output to a file name, in this case i’m saving the output to a file but you can just display the output to the screen by not specifying the re director.
You can add other options to the command to further customize its output, you can limit the number of results by using –l or you can use –e to specify a DNS server.
As you can see the information is straightforward and to the point, however, you may have the result larger than expected. You can limit the output of the command by using the grep command, for instance, you can only the emails that start with the letter “j” by using:
theharvester –d microsoft.com –b pgp |grep ^j
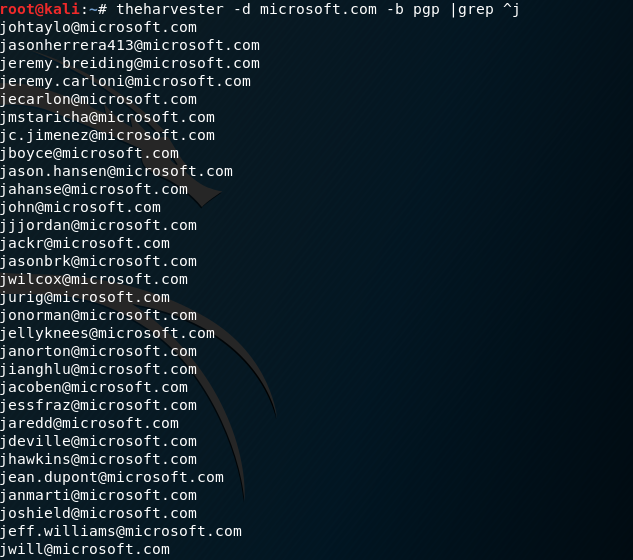
There’s more customization that can be made with the command but I’m sure by now you get the point.
___________________________________________________________________________
Linux-based security distros offer a great set of tools and utilities. Those tools are used by White-hat and Block-hat hackers. We’re JDTech, an IT support company in Northern NJ providing highly efficient, Network, WiFi, and Information Security Solutions and Services to businesses and organizations.