In this Cisco Meraki AirMarhal – Identify and Mitigate Spoofed SSID article I’ll show you how to the information detected by AirMarshal to locate the source of the spoofing access points.
You may also be interested in our Cisco Meraki WiFi troubleshooting article.
WiFi Network spoofing basics.
First, let’s talk about what spoofing is. In general terms, spoofing refers to creating “something” to impersonate an original. In other words, an attacker can spoof an email, IP address, or WiFi network to entice the recipient to believe that it is the original source. When it comes to WiFi, attackers can spoof WiFi networks by creating an unauthorized WiFi network (SSID) with the same name as the one that’s being targeted. The attacker can even take it to the next level by not only spoofing the SSID, but also by spoofing the mac address (BSSID) of the targeted access points.
WiFi Network Security.
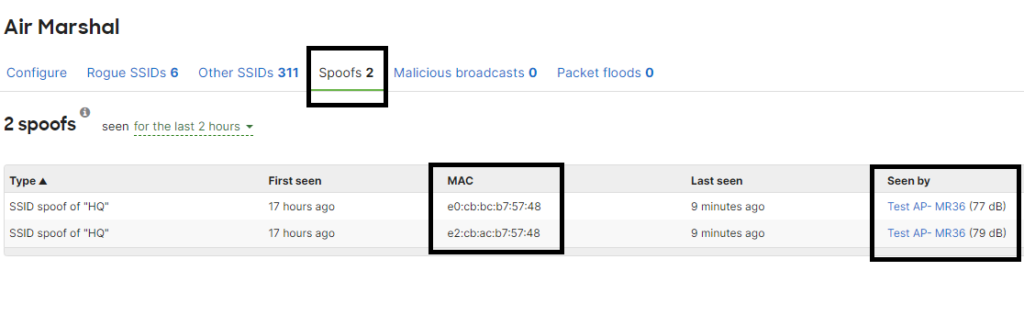
One of the most effective ways to monitor and protect your WiFi network is by implementing a Wireless Intrusion Detection\Prevention System (WIDS, WIPS). Cisco Meraki AirMashal is a powerful WIDS\WIPS that allows you to identify Rogue and Spoof Wireless networks. To protect your wireless network against spoofing you simply enable AirMarshal, once a Spoof network is detected it’ll display them in the Spoof Network tab.
Check our Meraki WiFi Best Practice – RF Profile customization article to learn more about Meraki WiFi.
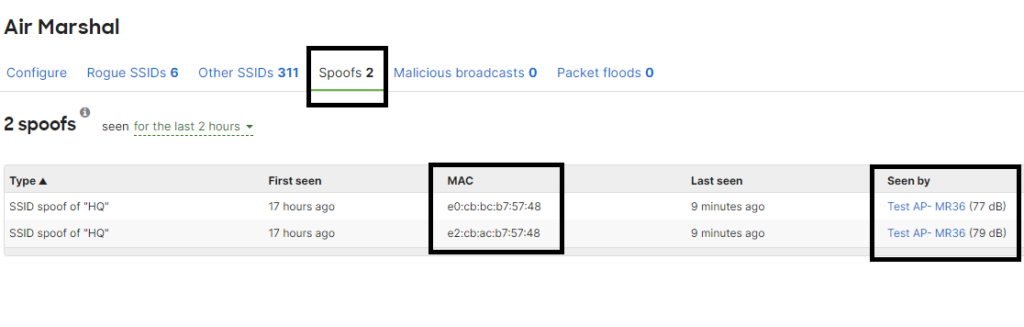
Something to keep in mind is that the Spoof option in AirMarshal does not allow you to contain the spoofing wireless network, but it provides information for you to identify the general area where the network is being identified for you to do “old-fashing” boots on the ground type of analysis and troubleshooting. You can also aid your troubleshooting by using a WiFi analyzer to identify the network and using the signal reading to get to the source.

Having the right tools and solutions in place will allow you to manage and secure your WiFi network, one of the great things about AirMarshal is that it does not require any special licensing for it to function, and if your Meraki access point supports the third antenna the monitoring and securing of the WiFi network will be without compromising WiFi network services to client devices.
We are the leaders in the planning and deployment of WiFi networks in New Jersey, with over fifteen years of WiFi and Security Services implementations, we have a proven track record of designing highly effective WiFi Solutions to businesses and organizations.
Contact us at www.jdtechsolutions.net, info@jdtechsolutions.net, or 646-500-0032 to learn about our solutions and services.