Meraki WiFi MAC-based authentication. Meraki, like other enterprise-grade network solutions, provides different types of authentication mechanisms. In this article, we’ll show you how to implement and configure Meraki MAC-based authentication using Windows NPS. Before we into the configuration we first need to understand how it works and why you would choose this authentication method.
When you implement Meraki WiFi MAC-based authentication you grant or deny network access based on the connecting device’s MAC address. This type of configuration requires a RADIUS server for the Meraki AP to query the user database for an access request message. The RADIUS server can admit or deny the device based on the MAC address, responding to the Meraki AP with either an Access-Accept message or an Access-Reject message, respectively. The configuration does not require user interaction or any type of special configuration on the client-side, and once it works it is a stable solution.
As useful as Meraki WiFi MAC-based authentication is it does come with its own set of challenges or rather vulnerabilities. The major weakness it has is that it’s easy to spoof a mac address. If an attacker changes the mac address of the device he’s using to an authorized mac address he will connect to the network unchallenged. In cases like this administrators may want to implement extra security measures to protect the network in the event of a security breach.
Perhaps you may be asking yourself why would I want to implement this type of access control? The truth is that would you more of a necessity than an option. The main purpose of Meraki WiFi MAC-based authentication is to support devices that can’t handle any other type of authentication, this usually includes legacy WiFI devices still used in productions environments. We see this type of deployment in warehouses, distribution centers, and hospitals that need to support old Wireless devices for specific reasons. Also, they can mitigate the likelihood of a breach by controlling SSID deployment to ensure that the networks configured with Meraki WiFi MAC-based authentication are only broadcasted in the specific areas where it is required – You can read more about SSID Allocation in this article -.
There’s no special licensing or equipment required for Meraki MAC-based authentication other than a RADIUS server and a Windows active directory. With that being said, let’s go over the steps required to implement Meraki WiFi MAC-based authentication using Microsoft NPS.
Create a NPS Policy for Meraki WiFi MAC-based authentication.
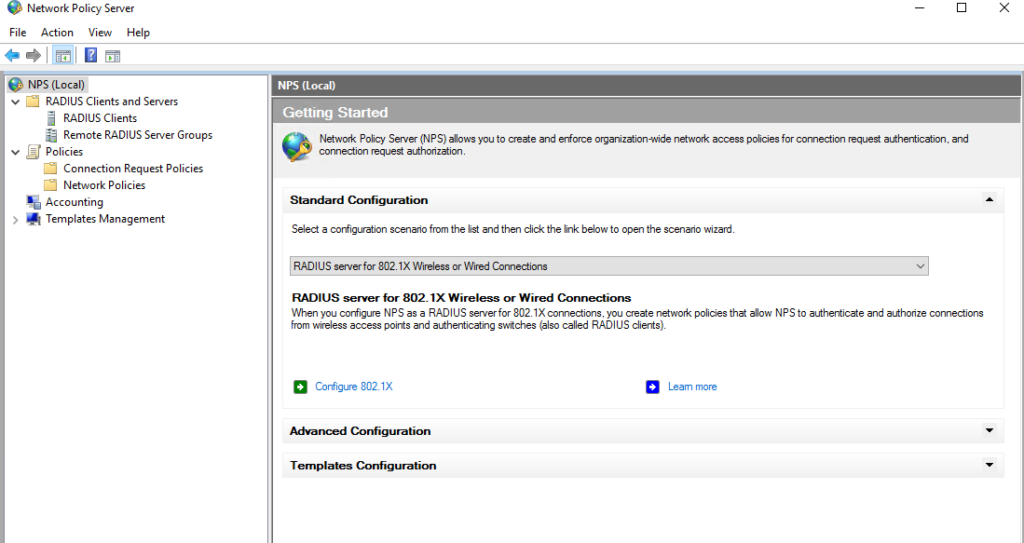
- Select the NPS (local) tab Configuration wizards.
- Make sure the RADIUS server for 802.1X Wireless or Wired Connections is selected. Click on Configure 802.1X
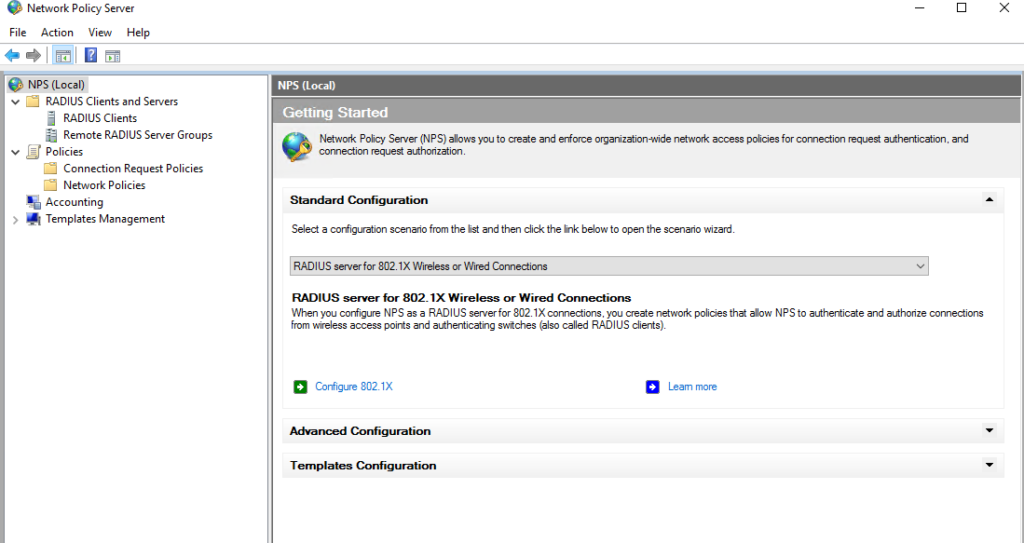
- Select Secure Wireless Connections
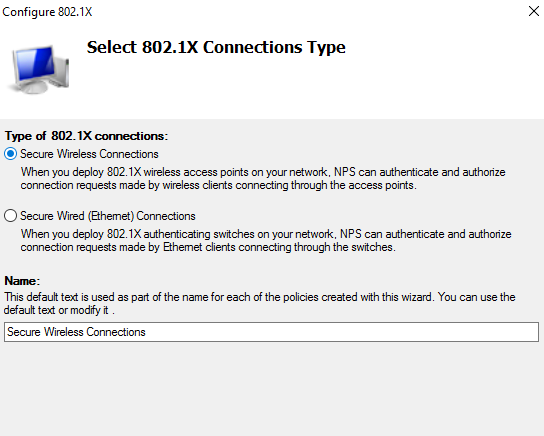
- Make sure you have a Radius client to serve the devices.
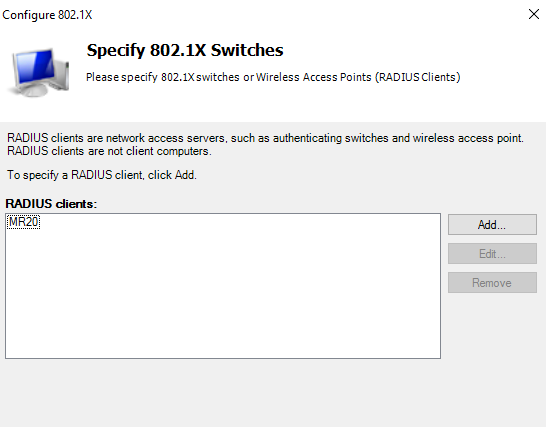
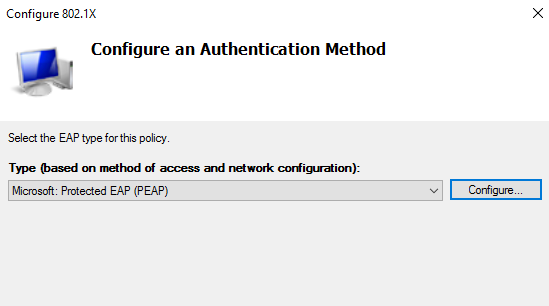
- For Configure an Authentication Method – Select Microsoft: Protected EAP (PEAP)
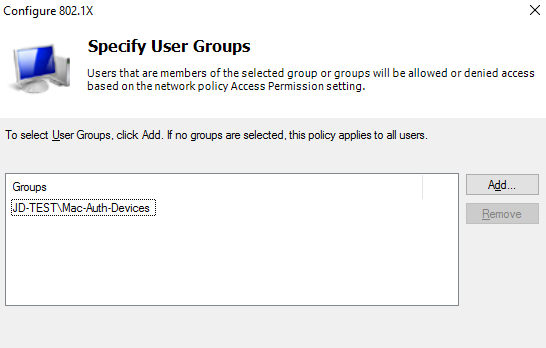
- Specify User Groups – Add the corresponding AP group.
- Configure Traffic Controls – click next. Then Finish.
- Edit the Newly created policy by going to NPS\Policies\Network Policies. Right-click on it and select properties.
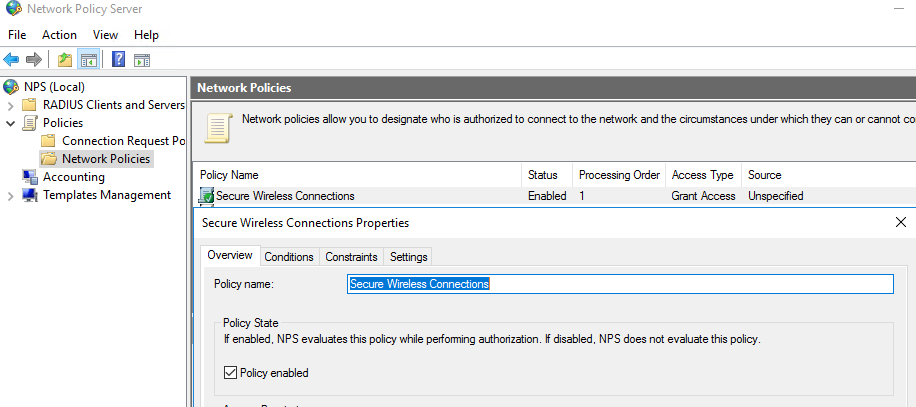
- Select the Constraints tab, Select Authentication. Select Unencrypted authentication (APA, SPAP)
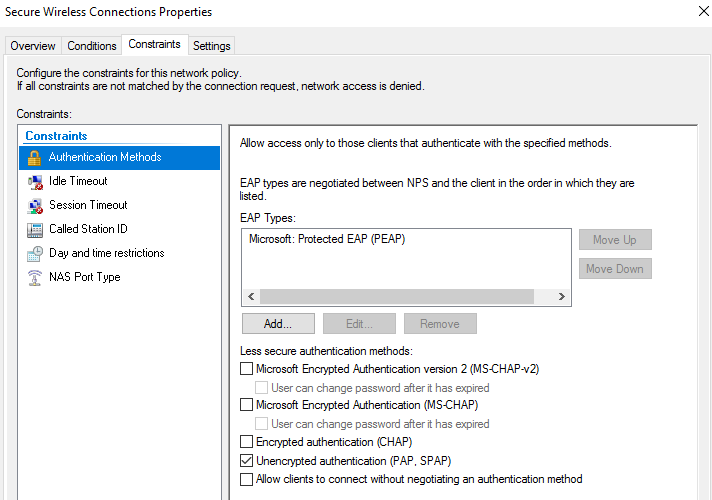
Create a User account for devices in AD for Mac-based authentication.
- Make sure you use the MAC address as the username and password. Add user to the AD group you specified in the 802.1X configuration.
*** Keep in mind that this may conflict with the Domain password policy ***
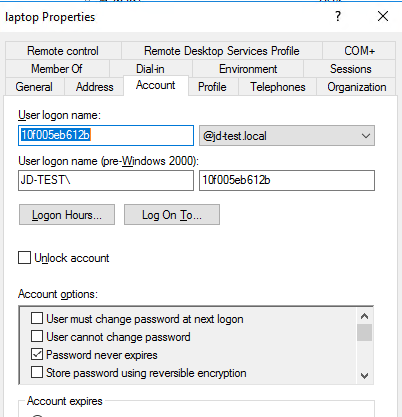
- Make sure the user belongs to the corresponding group you specified in the NPS policy.
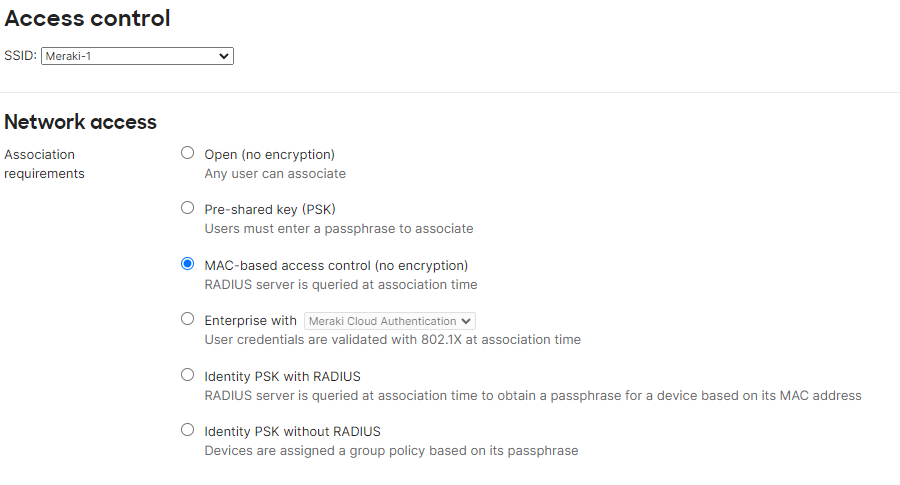
Configure Meraki SSID Access Control settings.
- For Network Access Control – Select MAC-based access control (no encryption)
- Scroll Down and add your RADIUS server.
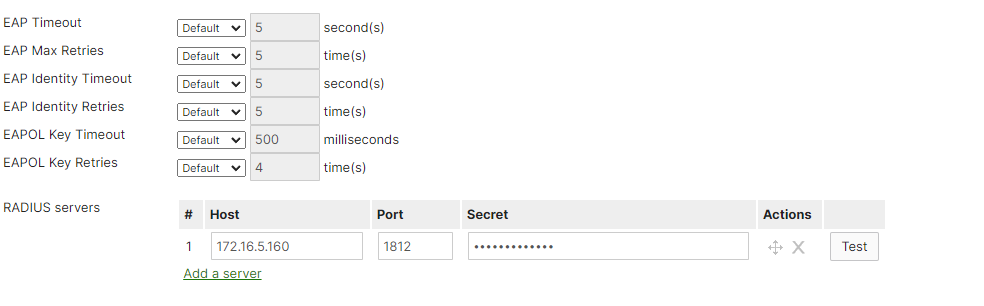
- Optional – Test the connection between Meraki and the NPS server by entering the mac address of the device (user).
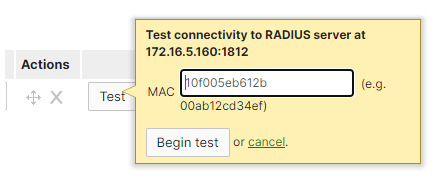
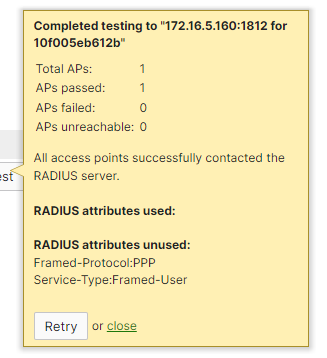
- The test result will notify whether the configuration is correct or not.
You can watch this and other configuration best practices on our youtube channel. IT Best Practices.
Wireless deployment requires higher levels of monitoring and administration compared to wired networks. Constant monitoring and adjustment may be necessary for most WiFi networks for reasons outside your control. That is why having the right Wireless Infrastructure in place that allows in-depth configurations is essential for reliable WiFi connectivity. We only work with the leader WiFi vendors because they provide the technology and support required for reliable and highly efficient WiFi solutions. When it comes to WiFi network deployments, JDTech is the leader in WiFi installation services in New Jersey and surrounding areas.
Contact us for details about our services and solutions at 888-580-4450, [email protected], and by visiting our website www.jdtechsolutions.net