As I mentioned in the WiFi or Ethernet article WiFi is an extension of the Ethernet network and each technology complements the other and creates one network.
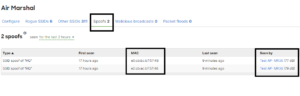
An interesting aspect of WiFi is that in its simplest implementation it is broadcasting your network information and the only layer of protection many companies implement is simply a password. You may think that because you have a strong password no one would be able to guess it and gain unauthorized network access to your network and its resources but in reality that is very far from true.
A few years I wrote a useful article with 12 tips to create a strong password, it mentioned the options of thinking in terms of passphrase where you use more than a single word as a password or even use a password generator. Let’s say that your WiFi password is indeed considered strong from a technical point of view, meaning no plain text, you have a combination of upper lower case, numerical symbols, numbers, punctuation marks, etc. Even if that’s the case relying on a password as the only protection against unauthorized network access is simply a false sense of security as with enough time and resources any password can be broken. There’s an abundant of online videos showing how to crack WiFi password even if you have little or no cyber security experience, although most of them oversimplify or show useless techniques and utilities there’s no doubt that there are plenty of available tools and tutorials anyone can follow to crack a WiFi password.
My point here is not for you to create a strong password for your WiFi network, gosh, that is a given and I really hope the password you’re using is complex, the point is to implement a higher level of security that even if a layer is compromised other layers would need to fall before an attacker can gain useful access to a network resource.
As always, the level of protection must be in the correlation of the resources to be protected. There’s no point of having a high insurance premium on a vehicle worth two pennies, likewise if the only resource to be protected is simply gaining unauthorized WiFi access through your router you may want to implement only the solutions that apply to it.
For that, I’m going to mention a few topics for best practice network security.
Separate Guest and Production network.
I’d say this is creating networks 101, you don’t want to have your visitors connect to your office network. Even if no one would be poking around having such a setup can easily introduce malware and viruses in the office environment.
Segregate traffic using VLANs.
This is the next logical step to network security, not only have Guest WiFi separate from the production network but only make sure the traffic is separate as well. This can be accomplished by the use and implementation of VLANs.
Implement 802.11x authentication.
It can be implemented at the router level or using Radius or Windows Active directory.
Provide network access on a need-to-know basis.
If you host a file server in your office make sure the proper file access permissions are implemented, what does it have to do with Wifi you may ask? With WiFi nothing, it has to do with security so even if your WiFi security falls unauthorized users won’t be able to gain resources access.
Implement IDS\IPS solutions.
Most small business firewalls offer various security subscriptions that monitor network traffic, we implement Sophos’ XG firewall solutions in our customers’ network as it provides us with advanced monitoring and security capabilities.
Keep your logs. You want to the when\where\to\from every time there’s a security incident.
As you can see for many companies everything starts with WiFi, if still have doubts, just remember the Target hack that caused millions of credit cards to be compromised. WiFi signals travel beyond the physical boundaries and as such your network becomes susceptible to attacks without your knowledge and control. Having a good security solution in place will make sure that not only your network is protected but also the network resources.
We are WiFi and Network experts in NJ providing highly efficient, cost-effective WiFi network solutions. We implement WiFi solutions from Cisco, Meraki, Aruba, Cambium Networks, Ubiquiti UniFi, and many more leaders in the WiFi world. Our WiFi solutions are designed to offer the reliability and security that you can count on.
Contact us for details about our WiFi Solutions at 888-580-4450 | www.jdtechsolutions.net | [email protected]