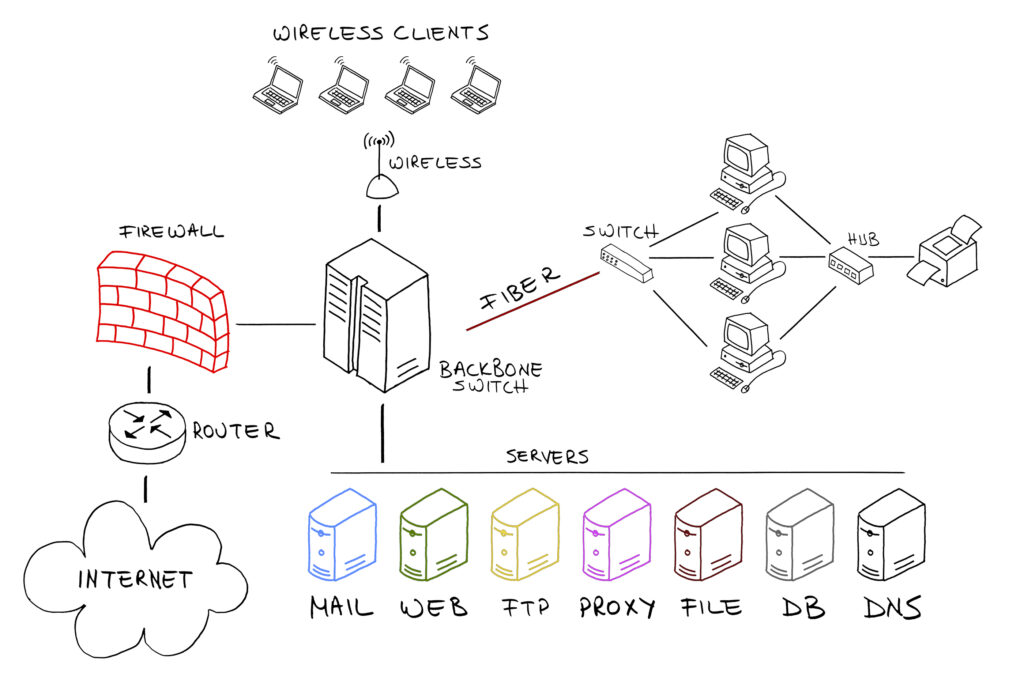
One of the most important network configuration settings in a corporate environment is the implementation of Virtual LANs (VLANs). VLANs allow administrators to create isolated broadcast domains within a physical environment, providing virtual benefits and functionality of having multiple networks –especially routers and switches -, but running on the same physical layer. VLAN implementation is unique to each company. Two of the most common categories for VLANs implementation are to separate VoIP and Data traffic. Further VLAN segmentation is usually implemented to separate traffic based on departments applications, devices, etc.
We recommend VLANs segmentation as part of the WiFi implementation to increase network security, manageability, and performance. When you implement VLANs, you have granular control of the network traffic; you can set firewall rules to allow\disallow access, implement QoS settings, and separate the traffic you see in your organization. All without the associated cost of different new network architecture.
Meraki offers simple ways to separate the Wireless traffic when deploying SSIDs, here are two of them:
- The first one – and more straightforward to implement – is by configuring the SSID to use NAT mode.
NAT mode configures the SSID in its isolated private network 10.0.0.0/8 segment. The setting prevents clients from communicating with each other, but clients could communicate with the internal networks if the SSID firewall settings allow it.
This type of traffic management is one of the most effective ways to deploy WiFi Guest networks in a corporate environment as it isolates on its WLAN.

As stated earlier, administrators can deny or allow the NATted to the internal network by implementing firewall rules. For a Guest WiFi network configuration, we recommend denying access to the LAN.
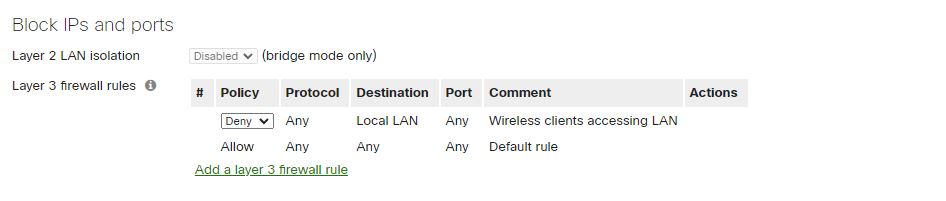
- The second option – we can say the most traditional – is by implementing VLANs.
When you want to implement SSID VLAN traffic segregation, you need to prepare your network environment for it. In the Meraki world, you need to access the Security & SD-WAN menu and select Addressing & VLANs. This is the Meraki menu that provides configuration options for your MX devices.
You first need to create a VLAN.
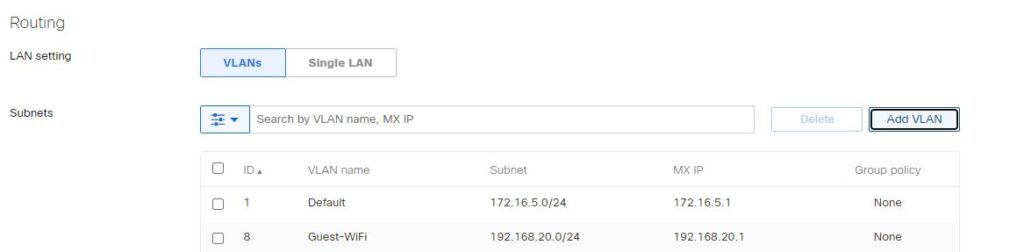
Then assign it to one of the ports.
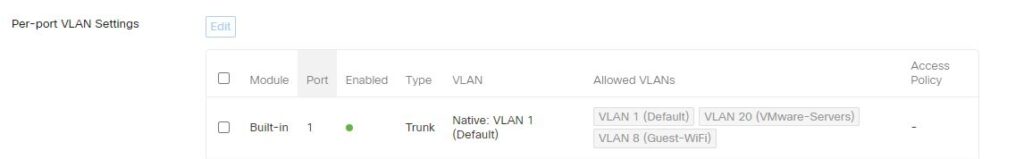
Other settings are necessary to implement the VLAN configurations successfully across your network. You need to create the VLANs in your switch’s configurations and Tag the ports where the APs connect. Each switch has different ways to do it. Let me know if you’d like me to create step-by-step instructions using Meraki switches.
Once you have the VLAN configuration in your Switches and Firewall\router device, you can configure your SSID to use the specific VLAN ID by enabling VLAN tagging and assigning the VLAN ID at the SSID level.
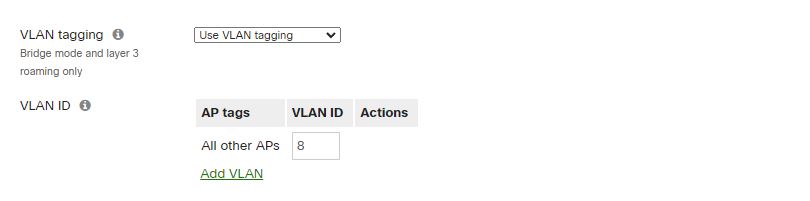
As you can see, Meraki offers two excellent for Traffic Segmentation. You should always consider segregating traffic in your company’s network infrastructure regardless of the size of the business, and when it relates to traffic traveling over the WiFi network VLANs offer an extra layer of security for your organization.
We are WiFi Experts deploying highly efficient WiFi solutions for businesses and organizations. We offer WiFi network consulting services, WiFi network design services, and WiFi implementation solutions.
You can contact us 888-580-4450 or [email protected] to talk to one of our WiFi engineers.