Bandwidth management is a priority for wireless administration, especially if you’re deploying multiple SSIDs with Corporate and Guest access. One of the many differentiators between hardwired and wireless LANs is that administrators usually apply more access controls settings to the physical LAN than the WLAN. For example, administrators manage the physical network connections in a corporate office environment, patching network ports to the switch when they need to be activated and un-patch them when they’re no longer in use. They also can enable or disable the switch ports as required, and implement other port-security configurations controls. That type of access management allows them to keep a tab of the number of concurrent connections, which will enable them to estimate bandwidth and resource utilization.
When it comes to WLAN, administrators have to implement different controls to achieve similar results. In the case of WiFi networks using pre-shared key authentication, anyone with a WiFi password can connect to the network, regardless if they are company employees or not. If they also provide guest access with pre-shared key or open authentication, anyone who knows the password or sees the network can connect to the network as well. Leaving the WiFi network unmanaged can wreak havoc on the overall bandwidth performance, affecting LAN and WLAN users alike.
Improve Multi-SSID WiFi environment with these best practices.
One of the most effective ways to mitigate bandwidth abuse in WLAN deployments is by implementing Bandwidth and Traffic shaping. Bandwidth shaping ensures that users don’t consume more bandwidth than they should by enforcing upload and download limits. The bandwidth limits can be enforced to users or SSIDs, even if clients roam from one AP to another. Traffic Shaping allows administrators to set bandwidth control based on applications, and they’re usually applied on a per-flow basis. Meaning that if you set a 3.5 Mps limit to four applications, the configuration will allow 3.5 Mbps to each application.
Let’s go over how Meraki does it.
Bandwidth Shaping.
Traffic and Bandwidth shaping rules under Wireless\Bandwidth and traffic shaping. The default setting is to allow WiFi connections unlimited bandwidth settings.
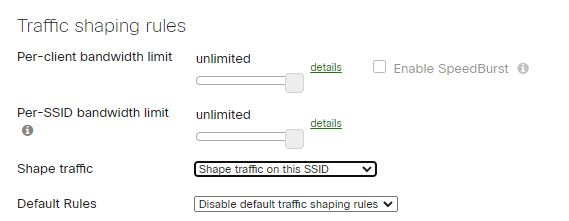
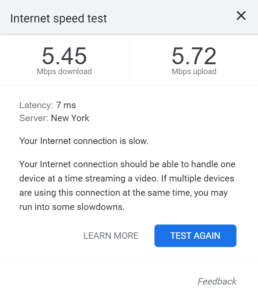
As you can imagine, such implementation in a WiFi network can be detrimental to the overall network person, with users and applications maxing out on bandwidth consumption. A speed test with an unlimited bandwidth limit shows clients utilizing all the bandwidth they can.
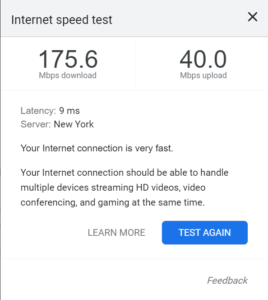
When we implement Traffic Shaping rules, we can apply them to Clients or to SSIDs. If you apply them to clients, each client will max at the pre-determined setting. If applied to SSIDs, clients’ bandwidth utilization can vary depending on the SSID performance, but they’ll be limited to the SSID setting.
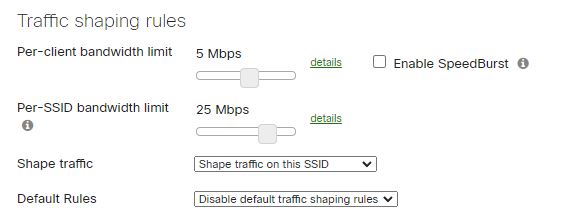
Applying the client settings will reflect on the WiFi connections.
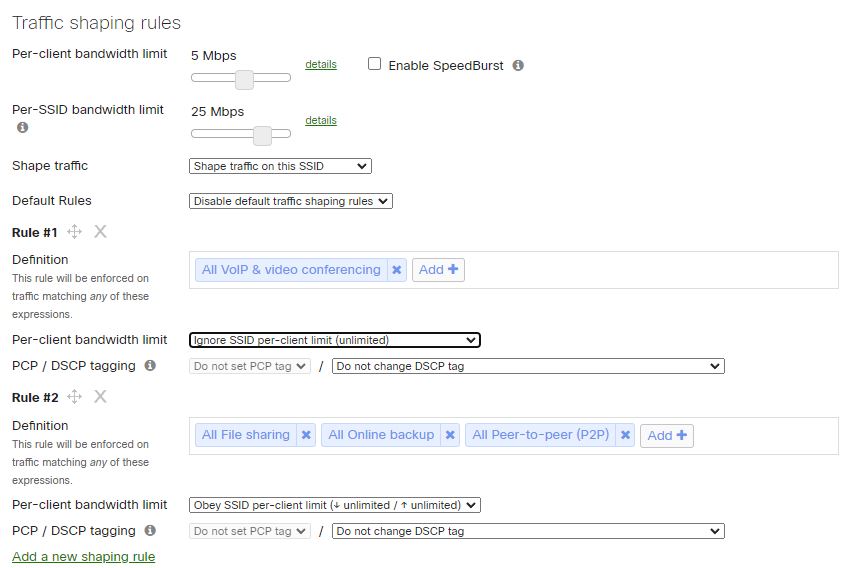
Traffic Shaping.
Bandwidth shaping offers the ability to control utilization at a network level, but as useful as it is in a WLAN deployment, it does not provide the flexibility to prioritize traffic while keeping the lid down. After all, you may want to limit the amount of bandwidth online backup and peer-to-peer applications without affecting other business applications such as video conferencing and VoIP.
That’s when Traffic Shaping comes into play, to help manage bandwidth utilization at the application level while still applying the traffic shaping rules. With Traffic Shaping rules, administrators can customize application-level policies to bypass the traffic level restrictions, rules are processed and applied to the network traffic in the order in which they appear. The action is also customizable, you can
1. Ignore any limits specified for a particular SSID.
2. Obey the SSID limits.
3. Apply more restrictive limits than the SSID limit.
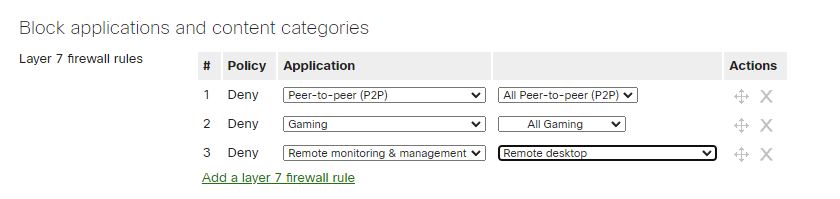
Layer 7 Firewall Rules.
Another level of Bandwidth and Traffic management available offered by some WLAN vendors is the implementation of Layer 7 Firewall Rules. With layer 7 firewall rule at the WLAN level, another level of Bandwidth and Traffic management available offered by some WLAN vendors is the implementation of Layer 7 Firewall Rules. With layer 7 firewall rules at the WLAN level, administrators can implement another layer of security and traffic management by inspecting the application layer and Deny traffic based on applications or application categories.
Implementing bandwidth and traffic shaping rules to a WLAN deployment is necessary for optimum network performance; it allows you to add a security and management level that could negatively impact the network performance if left unattended. Most WLAN vendors offer some type of bandwidth shaping configuration, but only enterprise-grade vendors such as Cisco, Meraki, Extreme Networks, etc., offer Layer 7 and traffic shaping options. Cisco and Meraki also provide an extra level of protection by implementing DNS layer protection, or as they call it, Cisco Umbrella. Cisco Umbrella goes beyond the point of this article, but it’s undoubtedly organizations should consider enhancing their security posture.
We are network experts who love designing highly efficient and secure WiFi solutions. We support Wireless configurations for businesses and organizations in New Jersey and across the country by helping them implement smart WiFi solutions to support their users and applications. With over 25 years of experience, we are WiFi experts ready to help you with your WLAN needs.
We are WiFi Experts providing highly efficient WiFi services and solutions to businesses and organizations in NJ and surrounding areas. Our Wireless and Network solutions are designed to provide the reliability and services to support your users and applications, we customize the WiFi solution to your specific needs.
Contact us at www.jdtechsolutions.net, [email protected], or 888-580-4450 to learn more about our services.