We always recommend companies looking to implement, upgrade, or secure their Wireless networks to implement 802.1X authentication. Deploying 802.1X increases the level of security in the network by requiring certificate-based authentication methods that are more secure than password-based authentication, also known as Preshared-key (PSK) authentication. 802.1X is an IEEE standard for port-based Network Access Control that provides authentication mechanisms to devices and users in a LAN and WLAN. It allows you to ensure that LAN users are authenticated before connecting to the network or obtaining an IP address from the DHCP server.
As stated earlier, 802.1X is an IEEE standard, and as such, it’s a technology that can be implemented by any technical company as long as they adhere to it. Meraki switches and access points are 802.1X capable devices that can serve as the Authenticator in an 802.1X deployment; in other words, they can be configured to be the link between the clients and the authentication server.
The 802.1X Wireless configuration is relatively simple on the Meraki side. The bulk of the work is done on the Radius server side as Radius servers have different versions, and each implementation is unique. Microsoft’s Network Policy Server (NPS) is one of the most widely used Radius server versions. Microsoft’s NPS is a server role that provides many network connectivity solutions in a corporate environment, including Network Access Protection (NAP), Central network policy manager, and 802.1X authenticated wired and wireless devices.
Problems with WPA2 PSK.
- Encryption key (password) management.
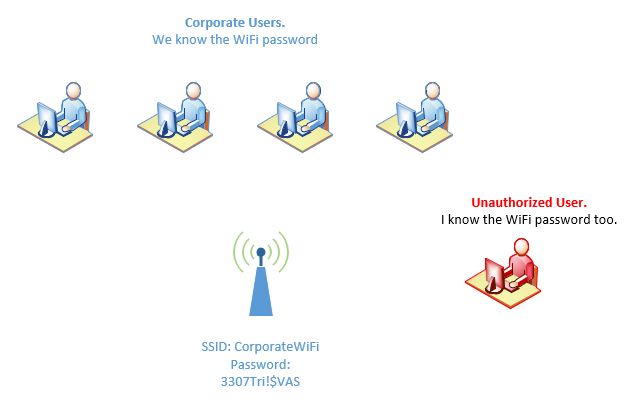
WPA2 Personal (PSK) is a WiFi-Alliance security standard to secure WiFi communication. It relies on AES to provide encryption services for data security and confidentiality. The WiFi world allows each wireless client to encrypt the network traffic using the encryption key (aka the password). This type of access solution is a thorn on the side of security administrators because there’s no real accountability as to who knows the password and who authenticates to the WiFi network.
- The security risk goes beyond network authentication.
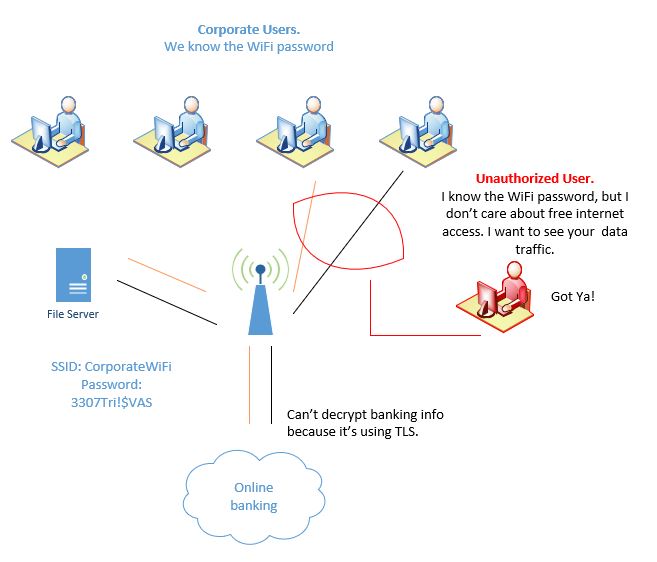
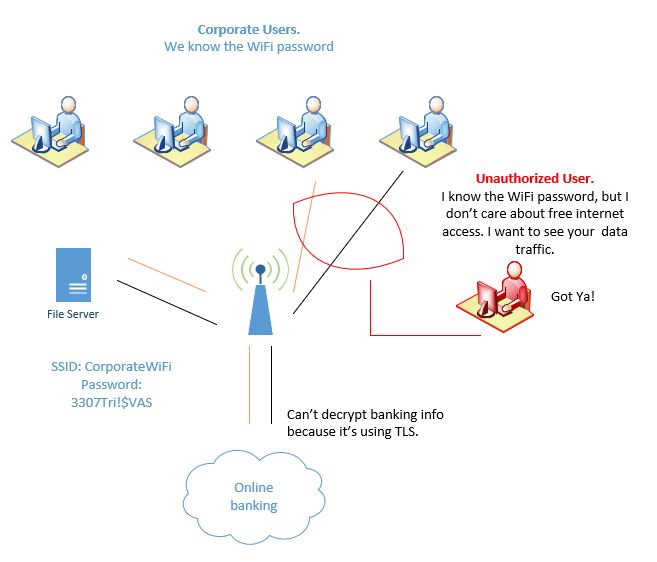
One may think the main risk on WPA2 authentication is that an unauthorized user may gain access to network resources, and as bad as it may be, the risk doesn’t stop there. When an intruder knows the WiFi password, they also have the decryption key; an attacker can potentially sniff and monitor intercepted encrypted WiFi traffic and display it in plain text. The illustration below corporate users accessing the WiFi network and network resources, because WPA2 PSK is implemented, administrators are not aware there’s an unauthorized user accessing network resources as well.
- Knowing the WiFi password is having the decrypting key.
With the decryption key, the attacker can read captured information in plain text. Keep in mind the attacker will be able to decrypt only the information encrypted with that key, even when the attacker is able to all capture the traffic from the victim, but once the attacker has gained network access it’s a matter of time before other systems get compromised.
So, what can you do in your Meraki WiFi solution to improve network security?
The answer to the question is by implementing 802.1X. Again, 802.1X is a standard, not a Meraki proprietary solution, and as such it’s available to all WiFi vendors that support it.
In order for you to take advantage of 802.1X on your Meraki WiFi solution, you first need to have a Radius infrastructure in place. When the Radius solution is in place you can configure the SSID to pass authentication requests to the authentication server through the Radius protocol.
The following illustrations show you how to configure Microsoft Network Policy Server (NPS) and how to configure Meraki WiFi solution to use Radius authentication.
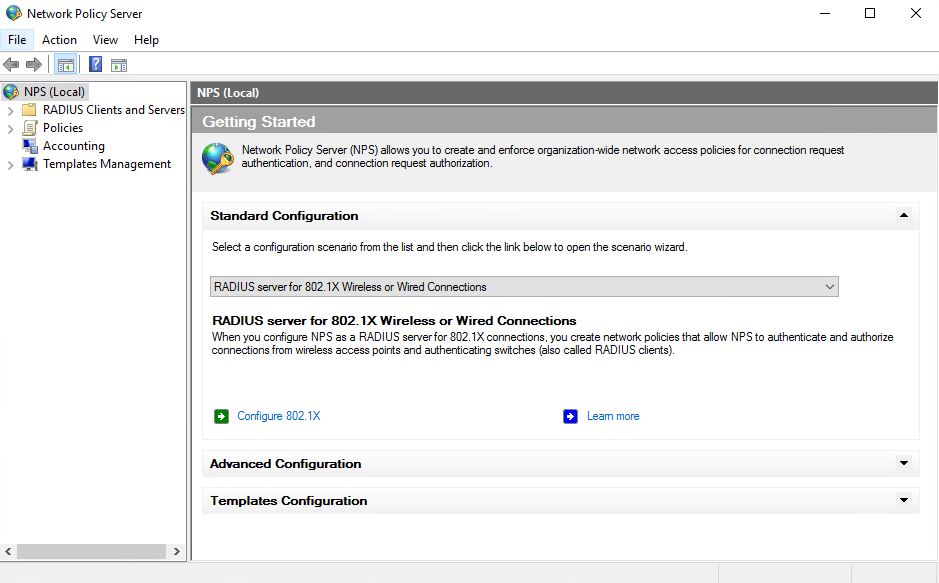
Install and Setup NPS role.
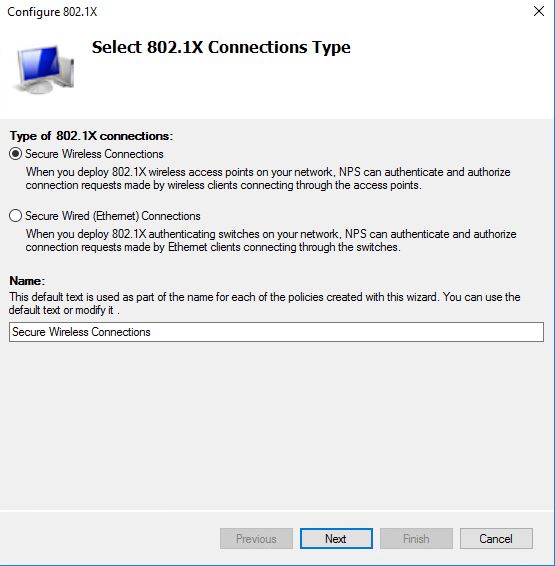
Select the Secure Wireless Connection option.
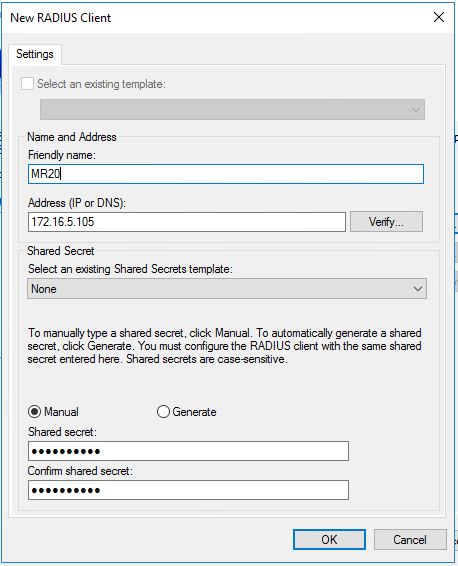
Enter the IP of the Radius Client (Access Point) and create the Secret Password.
Select Microsoft Protected EAP as the EAP type.
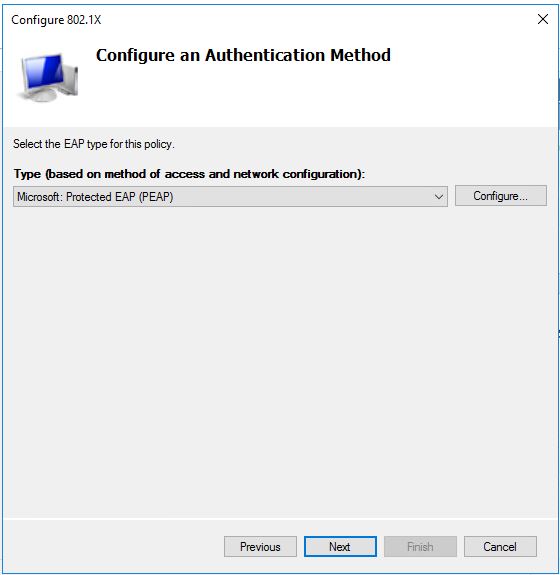
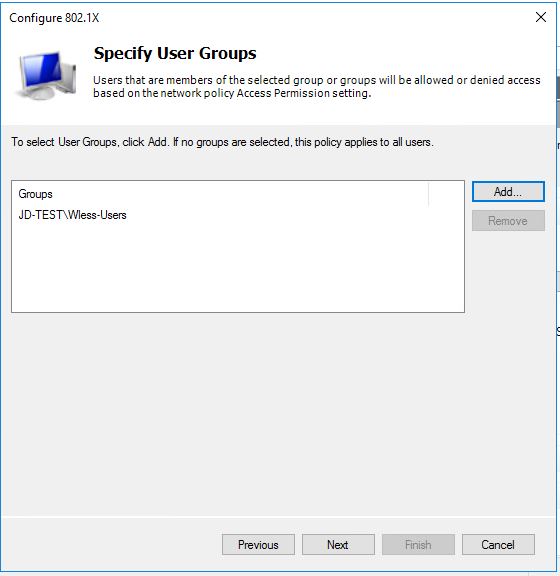
Specify the AD group to have the policy applied to.
Configure Meraki for 802.1X authentication
Configure the SSID for 802.1X authentication
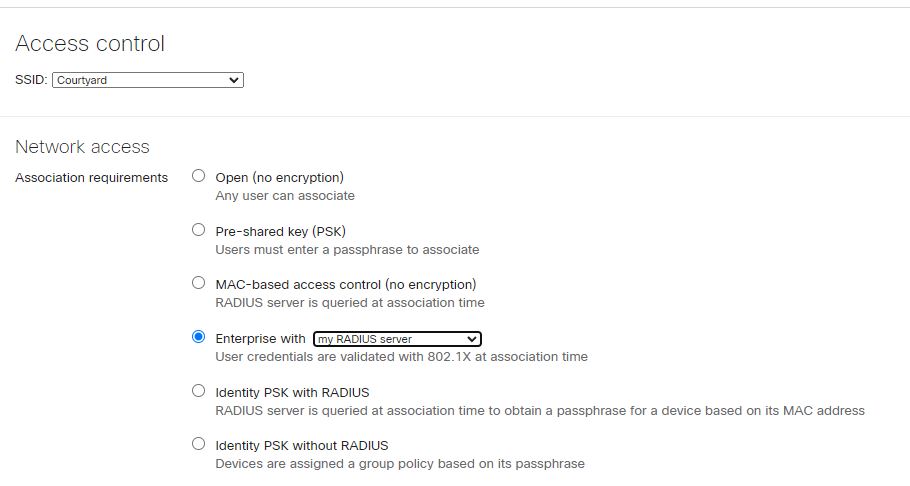
Configure Radius on Meraki SSID settings
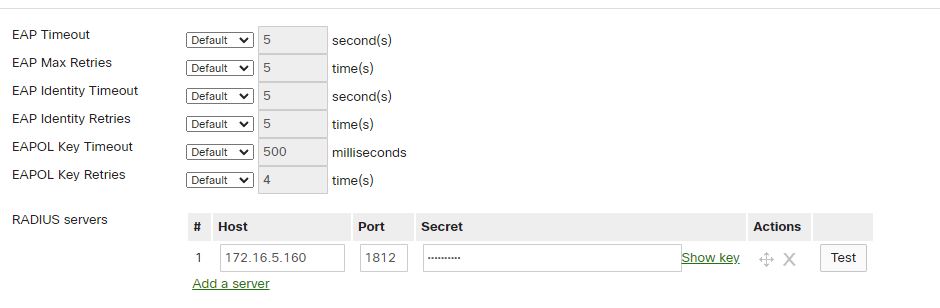
Once 802.1X is configured, you can log in to the network using your AD credentials.
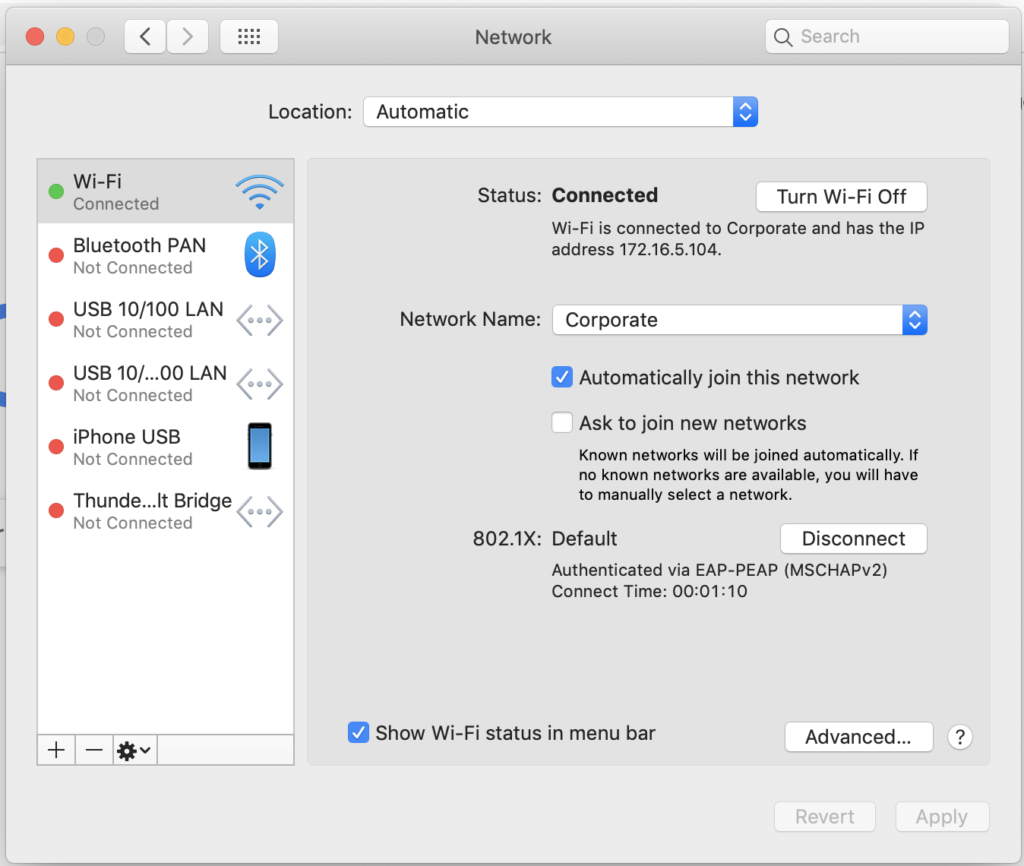
Implementing 802.1X authentication in a corporate network provides a higher level of security, accountability, non-repudiation, and management compared to WPA2 PSK. Although it provides greater benefits, 802.1X does not mean that a WiFi network using it is bullet-proof, there’s no such thing as 100% secure.
We are WiFi Experts providing highly efficient, reliable, and cost-effective WiFi network solutions. Our WiFi services and solutions include WiFi technologies from Meraki, Cisco, Extreme Networks (Aerohive), Ubiquity UniFi, Cambium Network, SonicWall, Sophos, and Fortinet. As WiFi experts, we implement the WiFi that makes sense to your unique environment.
Contact us for details about our WiFi services and solutions at 888-580-4450 or [email protected].