We have written before about the benefits of implementing Radius (802.1X) in a WiFi network configuration. In our Configure Meraki WiFi 802.1X authentication blog article, we show you the benefits of using Radius authentication and how to configure Meraki WiFi access with Windows NPS. As mentioned before, implementing Radius 802.1X in a WiFi environment has tremendous benefits for the administration, management, and security of the network. In this article, we want to show address the more important benefits 802.1X WiFi authentication offers in a Wireless deployment. The three significant benefits are 1. SSID consolidation, 2. Reducing Wireless Network Noise, 3. Key Management. The benefits list continues, but we’ll look at those three in this article.
- SSID Consolidation.
SSID broadcast generates all kinds of Wireless traffic, even when no one connects to them. Depending on the WiFi configuration and your environment, traffic from your WiFi network and the WiFi networks in the vicinity can saturate the WiFi spectrum.
Wireless Access Points follow the 802.11 standard, which dictates the WiFi communication in a network; as the WAP in your configuration and those around you follow the same rules, you’ll find that interference is created when Access Points follow the broadcasting rules. In the 2.4 GH band, there are only three non-overlapping channels (1,6,11). Access Points broadcasting SSIDs on the 2.4 GHz band will try to use those channels as long as there’s room for them. When the WiFi network is saturated with WAP broadcast over the same channels, they adjust to the environment and broadcast on the non-stander overlapping channel. This type of behavior is detrimental to a WiFi environment because having multiple SSIDs broadcasting on the same channel creates co-channel interference (CCI) and adjacent channel interference (ACI).
The network capture below is a perfect example of CCI and ACI interference in the 2.4GH band. As you can see, there are multiple SSIDs on channels 1, 6, and 11. But because of network saturation, some Access Points broadcast SSIDs on channel 3,7,9.
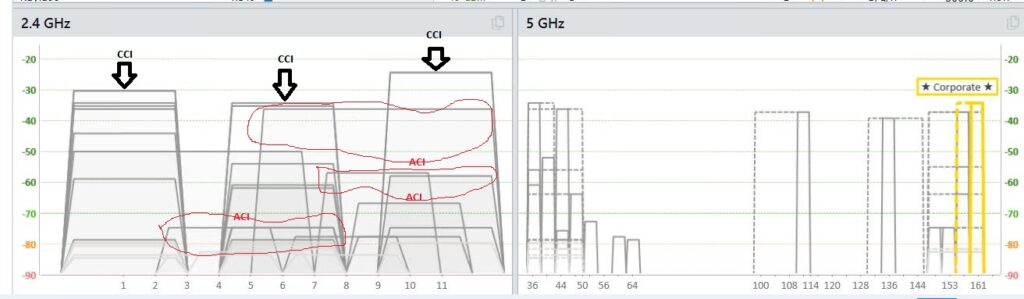
One of the main reasons for CCI and ACI is that too many SSIDs are contending for the main channel, and in the case of the 2.4 GHz band, the fight is more contentious due to the limited number of channels. That is the reason why is recommended to limit the number of SSIDs in WiFi configuration.
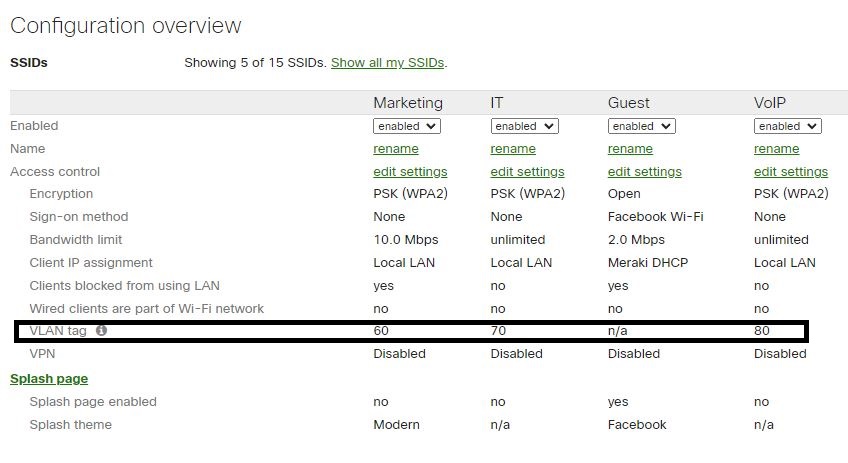
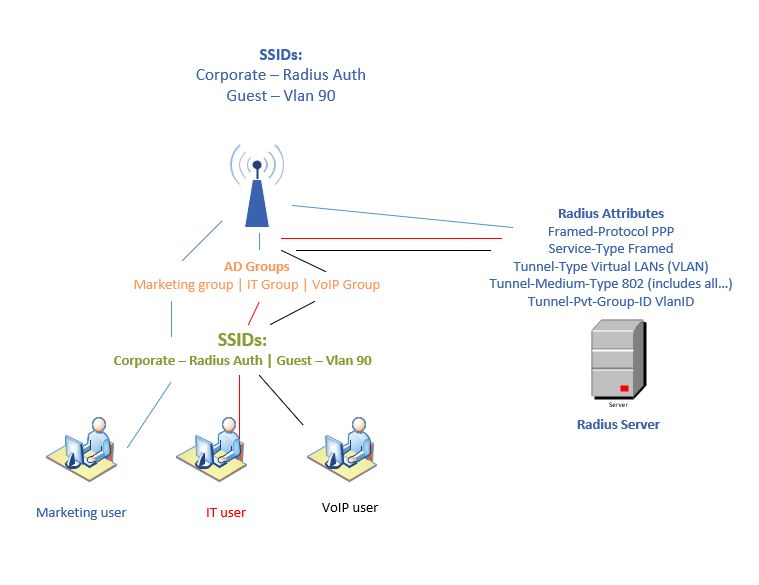
Implementing 802.1X allows you to consolidate multiple SSIDs into a single SSID, and by implementing Radius attributes, you can control segment traffic into different VLANs.
The example below shows a WiFi configuration with four SSIDs, each SSID map to a different VLAN segment for management, security, and compliance purposes. There’s no set number on the amount of SSIDs broadcasted by APS in a WiFi environment; WiFi best practice suggests no more than four SSIDs per radio, but that’s something to be determined during the WiFi assessment. Remember, Wireless traffic is generated by all kinds of WiFi and non-WiFi devices, whether they’re in your domain or not. That’s why it is a best practice to have a limited number of SSIDs.
2. Reducing Wireless Noise.
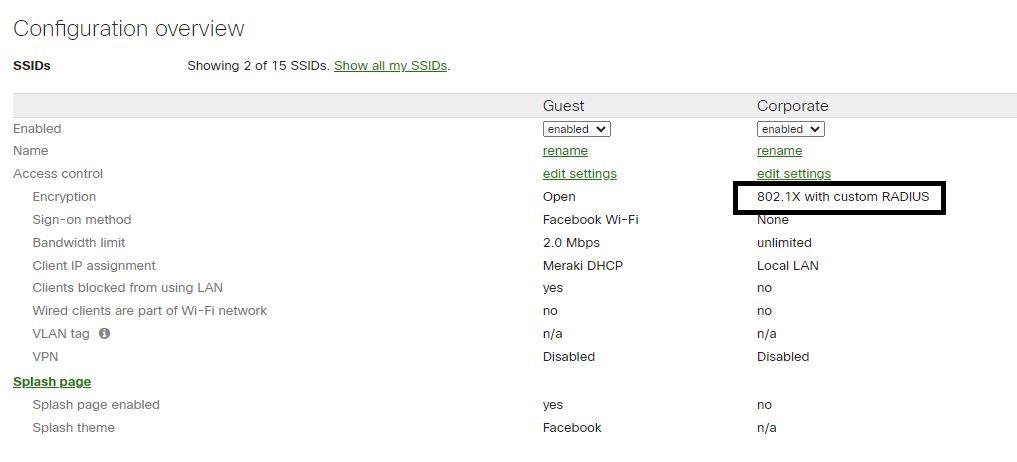
When you consolidate multiple SSIDs into one SSID by implementing 802.1X you help minimize the Wireless Noise in the spectrum, thus improving channel utilization and WiFI network performance.
We are WiFi experts who implement and support WiFi solutions from most vendors. We like how intuitive and straightforward the Meraki dashboard is to configure 802.1X. In this example, we have consolidated all other SSIDs into one SSID and use Radius attributes to map the VLAN segmentation.
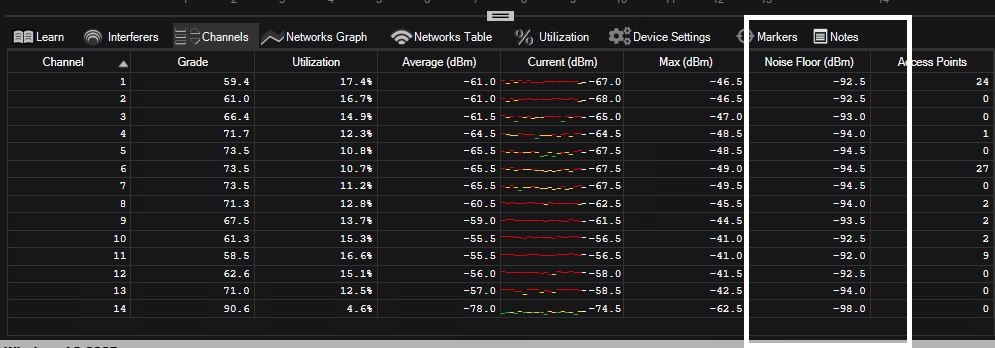
When lowering the amount of Wireless traffic in the network, the signal-to-noise ratio is improved. The Signal-to-noise ratio is a measure that quantifies how much the signal level exceeds the floor noise level. You want to make sure the noise levels are low, and one way to do it is by limiting the radio broadcasts that can have damaged 802.11 frames.
3. Key Management.
This is a real challenge for Wireless configuration using PSK. When the SSID is configured with Pre-shared key (PSK), users must enter a password – a shared password – to authenticate to the network. If the admins want to change the password due to password policy or because the password was compromised, they have to notify WiFi users of the changes. You can see how this becomes an issue in large organizations. Implementing 802.1X authentication is the solution to this issue because each user logs in with their unique network credentials. You can take advantage of active directory (if using AD) centralized administration and role-based access control to grant access to the network, including the WiFi network. If you need to terminate WiFi access, you can do it on a per-user basis without affecting anyone in the organization.
Those are the three of the benefits of implementing WiFi Radius authentication. Meraki offers more solutions for organizations that don’t have a Radius server infrastructure while offering similar benefits. You can implement 1. Enterprise with Meraki Cloud Authentication, 2. Identity PSK without Radius.
When it comes to WiFi Network services, you want to have a reliable WiFi expert by your side. We have over fifteen years of experience deploying WiFi, Network, and Information Security solutions to businesses and organizations. Whether you’re looking for a WiFi company to perform and Wireless Assessment to improve the Wireless network performance, or you need to engineer a new WiFi solution, you can count on us to deliver results.
Contact us for more details about our services at info@jdtechsolutions.net or 888-580-440