In our blog article WiFi best practice, Impvoe WiFi Performance and security with 802.1X Authentication, we explored the three main benefits of implementing WiFi Radius authentication with Meraki WiFi solution. WiFi Radius authentication is a great solution, but it’s usually a configuration for businesses with a more robust IT infrastructure that supports various types of servers in the configuration. A typical 802.1X infrastructure requires Radius, Directory Services, and Certificate services configured in the network environment. Such configuration also involves hardware, licensing costs, and a greater level of administration. There are many WiFi deployments (whether for small or large organizations) that require the main benefits of 802.1X Authentication but don’t have the ability to set up a Radius infrastructure, especially if the deployment requires WiFi security of IoT devices
Securing WiFi deployments without Radius.
Meraki offers a solution with similar benefits as Radius implementation, but without having a Radius server, the solution is called Identity PSK without Radius. It provides WiFi Security, more control over PSK, and in a proper WiFi configuration; it can also help the overall WiFi performance by improving the Spectrum utilization. It’s a WiFi Best practice that should be considered for companies without an 802.1X infrastructure.
IPSK without RADIUS allows a network administrator to use multiple PSKs per SSID without using a RADIUS server. Further, the feature allows you to assign group policies in the dashboard based on the PSK used by the client device to authenticate to the WiFi network. There is a limit of configuring up to 50 PSKs per SSID in Dashboard.
Let’s go over an example of Identify PSK without Radius configuration.
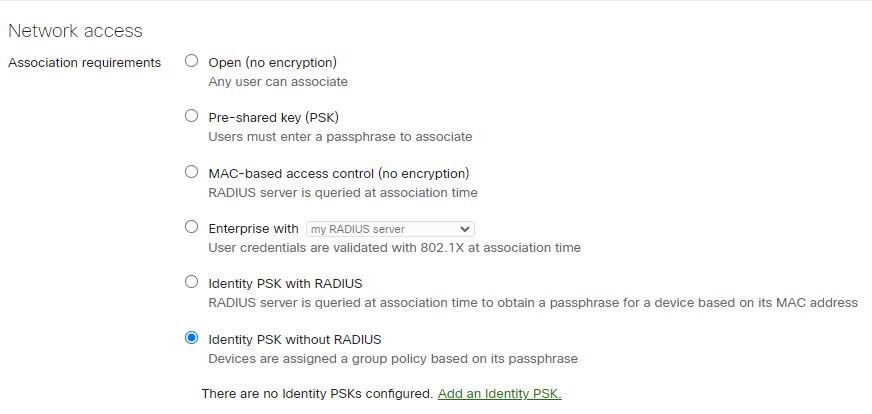
- Under your SSID settings, Select Identity PSK without Radius under Network access.
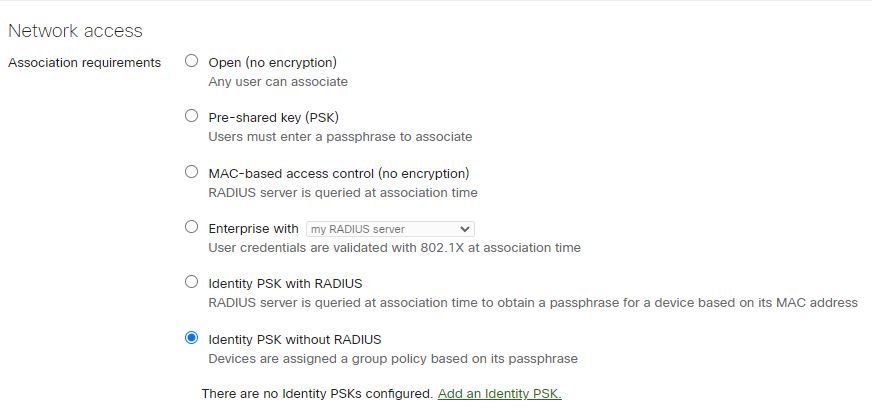
- Add the identity PSK option. Map the Identity to a Group Policy.
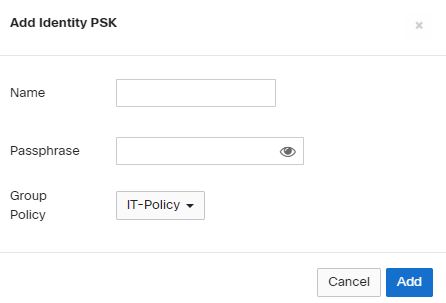
- If your Group Policies are not crated – Go to Network-wide\Configure\Group policies.
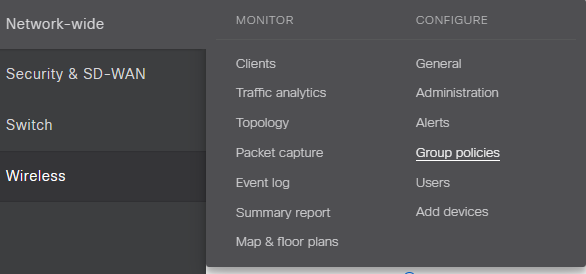
You will notice that the Group Policy settings are the same you would configure at the SSID level, you can implement the same WiFi Security settings you implement at the SSID level. You’ll apply your policies to the Identify Groups. Select the options that provide the WiFi performance for your deployment.
- Create the Identity Group and Apply the corresponding Policy.
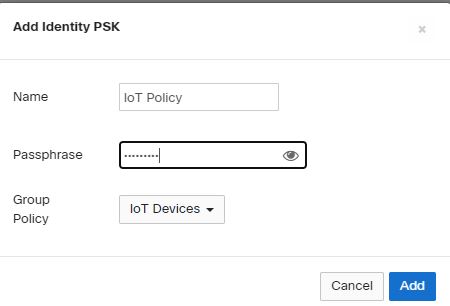
- Add and Save the configuration.
We have created a five Identity PSK in our environment, and each Identity is mapped to a Group Policy. Group Policies have the connections settings.
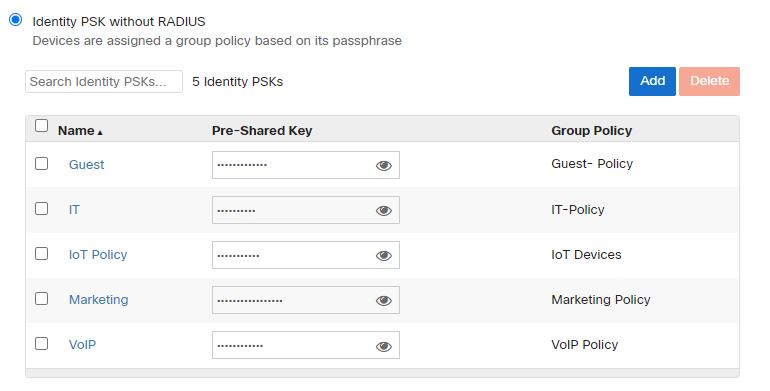
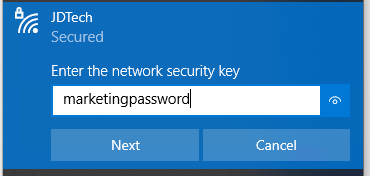
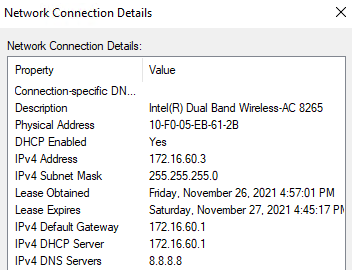
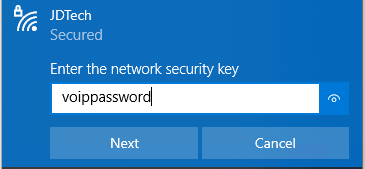
When Users authenticate to the SSIDs with the corresponding PSK Identity password, the Policy settings will seamlessly apply to the connection. In our example, we only broadcast one SSID – JDTech-. Users authenticate with the IPSK Group’s password. For example, Marketing IPSK password is marketingpassword, the Marketing Group Policy dictates that it belongs to VLAN 60. The VoIP IPSK’s password is voippassword, and its Group Policy maps the connection to VLAN 80.
Implementing Meraki Identity PSK without Radius configuration offers a more secure alternative to Pre-shared key (PSK) Authentication and simple alternative to Radius authentication while still providing a high level of WiFi security and improving WiFi performance.
We are a WiFi expert company developing highly effective WiFi network solutions for businesses and organizations in New Jersey and surrounding areas. Our experience and technical expertise allow us to implement WiFi best practices to any WiFi network infrastructure. Whether you are using Meraki, Cisco, Extreme Networks, Ubiquity, Cambium, or any other vendor, we can design and implement high-performance WiFi network configurations.
Contact us for details at [email protected] or 888-580-4450