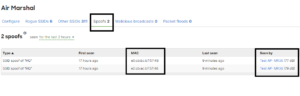
Small and large businesses, everyone is a potential victim of cybercriminals, as long as your

data is important to you cybercriminals are active “fishing” with hopes of trapping victims using one or many of their attack methods. We are cyber security experts, we have seen many companies fall prey to hackers simply for not properly implementing proper security measures. Here’s a simple list of five firewall services that can be configured to protect your network.
- Advanced Threat Protection (ATP): One the the main functions of ATP is to monitor outgoing traffic blocking network traffic attempting to contact command and control servers. This proven remote access trojan from contacting the controlling server.
- Intrusion Prevention System (IPS): monitors network traffic for malicious or suspicious activity as it passes through the firewall. IPS policies need to be created for the type of server that you’d like to monitor. Based on the information provided during the configuration the firewall is able to determine if traffic tofrom the server is suspicious or not.
- Web Content Filter: Controls the web content users are allowed to access. It’s a highly customizable feature that allows for granular control based on various criteria such as traffic type, source, destination, protocol, web site category, time of the day, etc. One of the main purposes of Web Content filter is to protect the network against attack vectors distributed via malicious websites.
- Application Control: As the name implies it allows the firewall administrator to control network applications or applications traversing the network. One of the most common uses is blocking remote control applications, proxies, vpn applications, stream applications, etc.
- Synchronized App Control:Is an advanced functionality to be used on top of application control because many application obfuscate in well known protocols such as http and https. On average 60% of apps go unidentified, synchronize security allows the firewall to identify all applications flowing through the FW.
Cyber security is dynamic, there’s no “one size fits all” when it comes to implementing network security, however, there are best practices for proper implementations. When securing your network always look at the firewall configuration, endpoint devices, and applications.
______________________________________________________________________________________________________________________________________________________
We are cyber security experts helping companies and organizations in northern NJ and NYC. Contact us about network and cyber security services for your organization.